Protect Your Employees from Potential State-Sponsored Risk with Shield
Blog
STRIDER
One of the most difficult aspects of managing state-sponsored risk is knowing what to look for. Seemingly innocuous communications and actions can fly under the radar until it’s too late. Strider Technologies changes that with Shield.
Shield is risk visualized. Properly implemented, it allows you to identify and resolve risks before they become serious problems. Here’s how Shield can support your insider threat and cybersecurity teams.
What is Shield?
Shield is a dynamic collection of data, including contact information and key words, that are directly connected to individuals, entities, and programs associated with foreign state-sponsored actors that are targeting commercial and other private organizations’ intellectual property.
Shield can be integrated directly into your current data loss prevention (DLP) system and flag any risky emails or other communication attempts. Shield is constantly updated with new and additional data every month.
What makes Shield different from other cybersecurity tools?
Shield is unique for several reasons.
- We do not require any client information. We only use open-source data to bring to light potential risk indicators.
- Because these state-sponsored actors use sophisticated and blended approaches, identifying their approach without contextual information can be extremely difficult. Shield delivers that context by offering insights from subject-matter experts on the tactics, techniques, and procedures (TTPs) of state-sponsored actors. Our subject-matter experts will help guide confident decision-making in your organization.
- Shield has extremely robust coverage, and it’s only expanding. Currently, we have over 12,000 selectors and terms that are used by state-sponsored actors.
How can you use the data from Shield?
Companies utilize the data from Shield in different ways.
- You can block all emails from individuals and entities listed in Shield.
- You can be notified when emails come from these individuals or entities. Once notified, you can investigate further on your own terms.
- You can also provide training to employees based on the domain names and terms that come through your system.
What does Shield look like in action?
Here are some quick examples of how Shield has helped our clients.
- Shield alerted Client A that an employee received an email from a restricted entity from the People’s Republic of China (PRC). Although this employee and team had been approved to work with this entity previously, the company reversed their decision after Shield notified them that the entity was on the sanctioned list.
- Client B’s Shield flagged numerous emails that were coming from individuals with ties to the Chinese Academy of Sciences. Shield revealed that these individuals belonged to a department that worked on the same technology as the client. The client deemed it too risky to continue receiving emails from these individuals, blocked further communication attempts, and provided extra training to the engineers. Without Shield, the client would not have known that the Academy was approaching their engineers in a targeted manner.
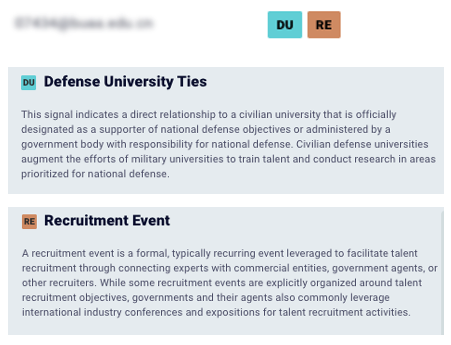
Shield’s database continues to grow
State-sponsored actors continue to evolve, and Shield evolves with them. Data gets refreshed and coverage gets expanded monthly. We regularly monitor the latest developments to ensure we provide the most current and accurate data points.
When you know where to look, risk is easier to identify. Shine a light on potential threats with Shield. Explore our product page to learn more.