State-Sponsored Risk
Proactively manage, visualize, and respond to state-sponsored risk at individual and industry levels

From quantum computing to wheat farming
Historically, state-sponsored actors mainly focused on collecting classified information at a government-to-government level. Today, they also focus on growing their strategic advantages through the global economy. That means collecting valuable information across a wide range of industries, like artificial intelligence, quantum computing, electric vehicles, and even agriculture equipment. As we have entered this era of geopolitical competition, many companies are at a heightened risk of state-sponsored intellectual property theft.

Understanding the
threat landscape
Awareness is the first step in creating a proactive defense response. To effectively secure your organization, you need both an external understanding of what information is being sought by rival governments and an internal understanding of how state-sponsored actors target your technology and talent.

Frequently Asked Questions
By reviewing foreign government strategic plans, economic goals, and economic statecraft policies, you can proactively know which technologies foreign governments are interested in. Insights offers an intuitive dashboard view of this information, and how it overlaps with the innovations at your own company.
One of the biggest challenges for internal threat teams is knowing where to best allocate their resources. Understanding how state-sponsored actors work and their recruitment cycle is critical to identify risk in your organization.
The state-sponsored recruitment cycle
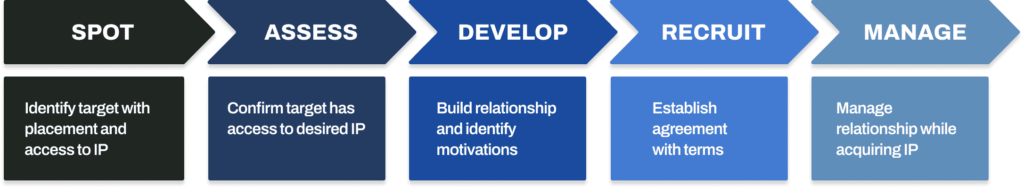
Using only open-source intelligence, Insights offers supplemental information on talent that’s at the highest risk of being targeted. This information complements your existing insider threat solution and provides crucial context in your investigations.
Strider products that can
solve this challenge:
Shield
After a bad actor spots and assesses a potential prospect in your organization, they need to make contact. Shield acts as a supplementary security tool that screens inbound communication from state-sponsored actors. With the ability to flag or block communication from known actors, you can effectively stop intentional and unintentional insider threat before it starts.
Learn MoreInsights
With Shield preventing initial contact of state-sponsored actors and Insights adding critical data to current potential risk, you can finally go from a reactive to a proactive defense response.
Learn MoreBetter allocation of time and money
With better insights of threats within your organization, you can more effectively and efficiently allocate time and resources.
Your internal data is not required
Strider collects data from tens of thousands of primary data sources in multiple languages through a zero-touch architecture, so we never require any of your internal data.
Uncover hard-to-detect threats
Strider’s customized dataset layered with our proprietary risk methodology offers your organization access to information that other security tools can’t provide.
Ongoing threat detection
With millions of new data points collected daily, we provide you with new and actionable insights regularly.